Written by Anneri Fourie | Crises Control Executive
A cybersecurity incident rarely announces itself neatly. One minute a monitoring alert flags unusual activity. The next, multiple client systems are affected, senior leaders want answers, and teams are working off different versions of the truth. Email threads multiply, chat messages contradict each other, and key decisions go undocumented.
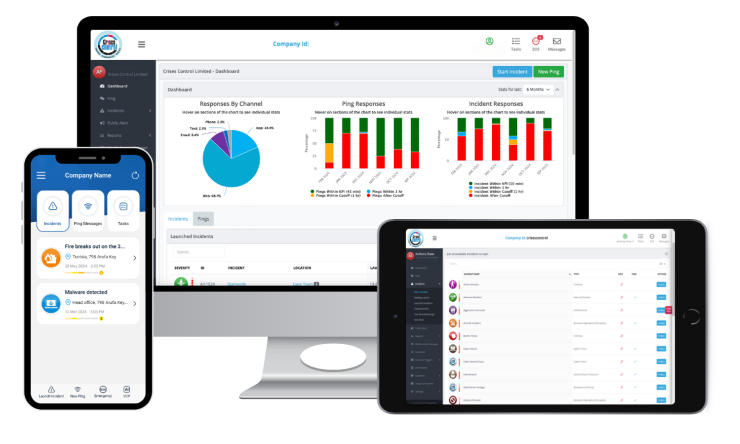
This is where many cyber responses break down. The technical teams may know what to do, but the organisation struggles to coordinate people, actions, and communication at speed. A Mass Notification System addresses this gap by providing a structured way to alert the right people, control information flow, and keep response efforts aligned from the first alert through recovery.
This article explains how emergency response should work during cybersecurity incidents, why coordination is often the weak point, and how organisations can move away from improvised responses towards repeatable, auditable processes.
Why cybersecurity incidents need a different emergency response approach
Cyber incidents spread across systems, teams, and borders far faster than most physical emergencies. A ransomware attack against a shared service can affect dozens of clients at once. A phishing campaign can compromise user accounts across regions within hours. A data breach may trigger legal and regulatory duties before the full technical impact is clear.
In practice, this creates predictable problems.
- Alerts remain inside technical teams for too long
- Executives receive fragmented updates from multiple sources
- Client-facing teams lack clear guidance on what to say
- Actions are taken but not recorded
- Evidence needed for regulators is reconstructed later under pressure
The issue is rarely a lack of skill. It is a lack of coordination. Emergency response for cyber incidents must focus on getting the right information to the right people, at the right time, using systems that still work when internal infrastructure is under strain.
Mass Notification System as the backbone of cyber incident response
What a Mass Notification System does during a cyber incident
A Mass Notification System provides a controlled, auditable way to mobilise response teams. It replaces informal alerts and scattered messages with a single mechanism that delivers instructions, tracks acknowledgements, and supports escalation.
During a cybersecurity incident, this means:
- Predefined response groups can be alerted within seconds
- Escalation happens automatically if alerts are ignored
- Messages are delivered across multiple channels, not just email
- Everyone works from the same verified information
- Communications are logged for later review
For IT services and consulting firms supporting client environments, this clarity is essential. Clients expect prompt updates. Leadership expects confidence. Regulators expect evidence.
Emergency Mass Notification System for Cybersecurity Incidents in real situations
An Emergency Mass Notification System for Cybersecurity Incidents must operate independently of affected systems. Many cyber attacks disrupt email, identity services, or internal networks. Relying on those systems to manage the response creates risk.
A practical notification platform supports:
- Cloud-based delivery that remains available during outages
- Incident templates for ransomware, breaches, and service failures
- Role-based alerts that follow agreed escalation paths
- Confirmation tracking to see who has acknowledged messages
- Secure audit logs that capture what was sent and when
Crises Control supports this approach by allowing organisations to trigger alerts from any device and manage response communication even when internal systems are degraded.
Interested in our Ping Mass Notification Software?
Efficiently alert everyone in seconds at scale with our Mass Notification Software.
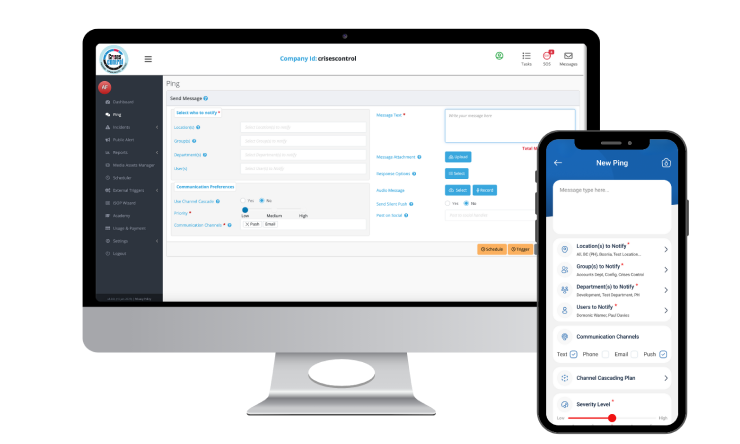
Incident Management Software for Cybersecurity beyond alerting
Alerting people is only the first step. Once teams are engaged, work needs to be organised and tracked. Incident Management Software for Cybersecurity provides the structure that keeps response efforts moving in the same direction.
Coordinating response actions under pressure
During a cyber incident, actions span far beyond technical containment. Tasks may include forensic investigation, regulatory assessment, client briefings, and executive decision-making.
Effective incident management supports:
- Clear task ownership with deadlines
- Visibility across technical and non-technical teams
- Secure collaboration without relying on compromised tools
- A live timeline of actions and decisions
Crises Control links notifications directly to incident workflows, ensuring that actions triggered by alerts are tracked and reviewed rather than lost in side conversations.
Crisis Management Software for leadership clarity
Senior leaders often become involved early in cyber incidents. They need insight, not raw data. Crisis Management Software provides structured updates that allow leadership to understand impact and make decisions without disrupting response teams.
This enables leaders to:
- See which clients and services are affected
- Track progress against response priorities
- Approve external communications before release
- Demonstrate oversight during internal and regulatory reviews
This separation of operational detail and executive visibility reduces confusion and helps maintain confidence across the organisation.
Business Continuity Software and cyber resilience
Cyber incidents often extend beyond initial containment. Systems may be unavailable for days. Client services may need alternative arrangements. Recovery planning must run alongside incident response rather than waiting until the end.
Business Continuity Software supports this by linking cyber response to continuity actions such as:
- Activating alternative processes when systems are unavailable
- Coordinating remote working or backup services
- Managing service restoration priorities
- Tracking recovery milestones
Crises Control allows continuity plans to be stored digitally and activated as part of the incident workflow, rather than sitting unused in static documents.
Emergency response plan for cybersecurity incidents
What an effective cyber emergency response plan includes
An Emergency response plan for cybersecurity incidents defines how an organisation reacts from detection through recovery. The most effective plans are practical, role-based, and accessible during an incident.
Key elements include:
- Clear criteria for incident classification
- Defined notification thresholds and escalation paths
- Assigned roles across IT, legal, communications, and leadership
- Guidance for internal and external communication
- Regulatory and client notification requirements
- Post-incident review processes
Plans that live only as documents often fail when pressure rises. Digital plans integrated into response platforms allow teams to follow steps in real time while adapting to changing circumstances.
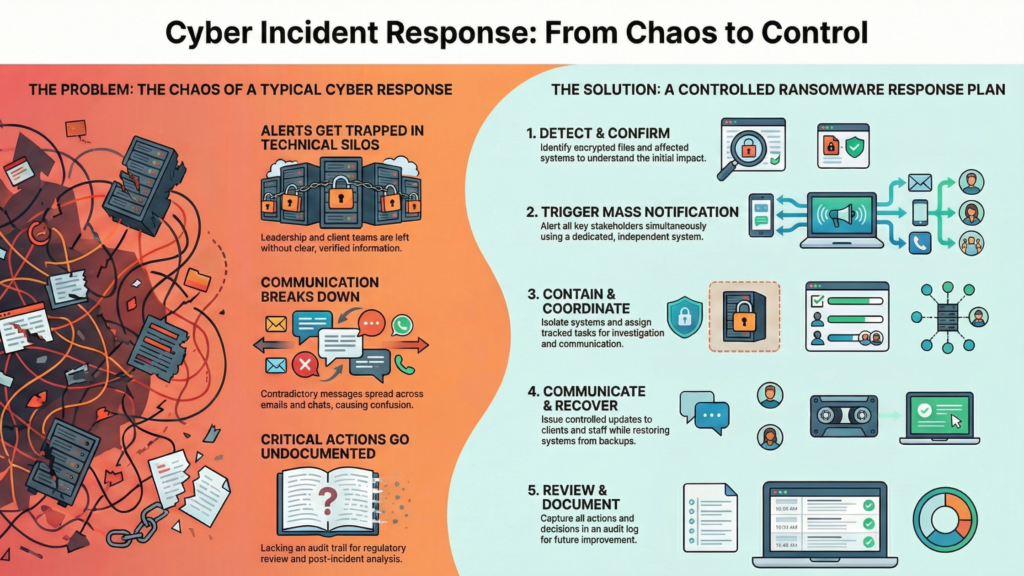
How to respond to a ransomware attack step-by-step
Ransomware remains one of the most disruptive cyber threats faced by IT services and consulting firms. A structured response limits damage and reduces long-term impact.
- Step 1: Detect and confirm: Identify indicators such as encrypted files or ransom messages. Confirm affected systems and users.
- Step 2: Trigger mass notification: Use a Mass Notification System to alert IT security, incident leads, legal, and leadership. Avoid informal messaging.
- Step 3: Contain the threat: Isolate affected systems, disable compromised accounts, and block further spread.
- Step 4: Coordinate response tasks: Assign remediation, investigation, and communication tasks through incident workflows.
- Step 5: Communicate clearly: Prepare controlled updates for staff, clients, and regulators. Ensure consistency.
- Step 6: Support recovery and continuity: Restore systems from backups, monitor for reinfection, and activate continuity plans where needed.
- Step 7: Review and document: Capture actions, decisions, and lessons learned using audit logs.
Crises Control supports this entire process by connecting alerting, task management, communication, and reporting in one environment.
Regulatory and client communication during cyber incidents
IT services and consulting firms often operate across jurisdictions. Cyber incidents may trigger obligations under GDPR, NIS2, DORA, or sector-specific rules.
Common expectations include:
- Timely notification to regulators
- Clear documentation of response actions
- Evidence of internal governance
- Accurate and consistent client communication
A structured notification and incident management platform reduces the risk of missed deadlines and incomplete records during high-pressure situations.
Testing and improving cyber incident readiness
Plans that are never tested rarely work as intended. Exercises reveal gaps in escalation paths, contact details, and decision-making.
Effective organisations use regular simulations to:
- Validate notification reach and response times
- Test leadership workflows
- Identify outdated plans or contacts
- Build confidence across teams
Crises Control supports scheduled exercises and captures performance data that can be used to improve readiness and demonstrate compliance.
Why IT services and consulting firms benefit from structured response platforms
IT services and consulting firms face a dual challenge during cyber incidents. They must manage their own response while supporting clients who may also be affected.
A unified response platform helps by:
- Separating internal coordination from client communication
- Assigning clear ownership across teams
- Supporting faster, better-informed decisions
- Reducing reliance on improvised tools
This approach supports trust, accountability, and operational stability during difficult situations.
Bringing everything together
Emergency response for cybersecurity incidents depends as much on coordination as technical skill. A Mass Notification System, combined with incident, crisis, and continuity management, provides the structure organisations need to respond with control and clarity.
Crises Control supports IT services and consulting firms by bringing alerting, workflows, communication, and reporting together in one platform. This helps teams manage cyber incidents from the first alert through recovery and review without losing oversight.
Speak to us about strengthening your cyber incident response
If your organisation wants to improve how it responds to ransomware, phishing attacks, and data breaches, Crises Control can help you move from reactive communication to structured, auditable response.
Contact us today to get a free personalised demo and see how Crises Control supports emergency response for cybersecurity incidents across your organisation.
Request a FREE Demo